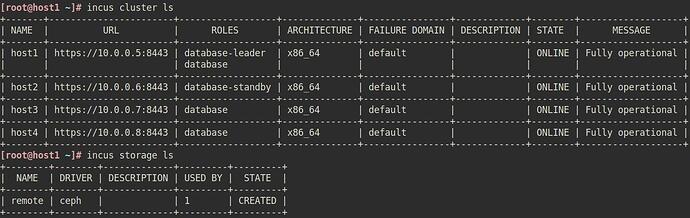
if you are running incus - you should also snap remove lxd
I did some more reading & network testing of wireguard (680 mbps) & a normal 1gbps interface (935mbps) - so it makes more sense to run microceph on the main interface firewalled to trusted ip’s on a small connection (unless you really want double encryption).
For the firewall allow tcp 3300 6800-6810 7443 & not tcp 6789 (the legacy v1 protocol) - 3300 is the new v2 messenger protocol which is end to end encrypted.
The dashboard doesn’t work at the moment on either https with a self signed cert or as http - & probably needs normal ceph configured to work properly. Again apparmor the most likely cause:
Nov 14 22:52:59 host1 kernel: [ 196.137689] audit: type=1400 audit(1700002379.659:34): apparmor="DENIED" operation="capable" profile="snap.microceph.mgr" pid=627 comm="dashboard" capability=12 capname="net_admin"
- Disabling
apparmorto ‘fix’ thedashboardis not an option asmicrocephrefuses to start without it - Enabling
prometheusalerts / metrics is probably sufficient