Hello! ![]()
I’ve been struggling with certain setup over the past few weeks. I have a VM instance running on Linux machine. The OS inside the VM is Windows Server with RDP enabled. I can connect to it on my local network no problem.
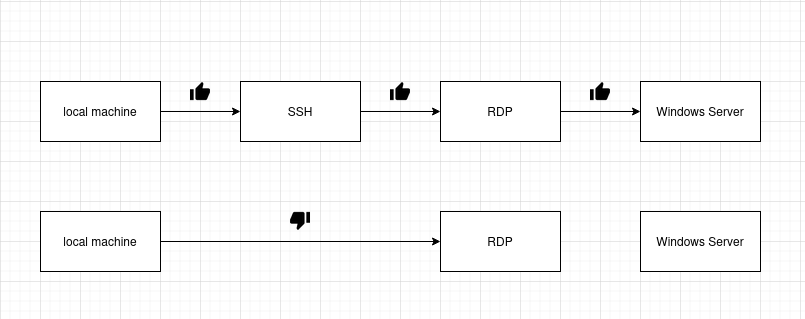
As I plan to host that machine in the cloud, I want to secure it from any brute force attacks that might happen. My idea is to use SSH as the entry point, so RDP can be accessed within the guest only if SSH session was established successfully to the host server.
This is the config of the VM:
architecture: x86_64
config:
limits.cpu: "4"
limits.memory: 8GiB
volatile.cloud-init.instance-id: 8855e2a9-f0e5-420a-acb1-fc00d32ff663
volatile.eth0.host_name: tap0161153f
volatile.eth0.hwaddr: 00:16:3e:c1:fc:12
volatile.last_state.power: RUNNING
volatile.uuid: dfb8663a-aadf-4c08-bef4-ddb1ed2a8831
volatile.uuid.generation: dfb8663a-aadf-4c08-bef4-ddb1ed2a8831
volatile.vsock_id: "2463382061"
devices:
eth0:
ipv4.address: 10.10.182.165
name: eth0
network: incusbr0
type: nic
port-3389:
connect: tcp:10.10.182.165:3389
listen: tcp:127.0.0.1:3389
nat: "true"
type: proxy
root:
path: /
pool: default
size: 40GiB
type: disk
ephemeral: false
profiles:
- default
stateful: false
description: ""
And iptables rules (same rules apply to IPv6):
Chain INPUT (policy ACCEPT)
target prot opt source destination
sshguard tcp -- anywhere anywhere tcp dpt:ssh /* SSH Guard */
ACCEPT tcp -- anywhere anywhere tcp dpt:ssh /* SSH */
ACCEPT udp -- anywhere anywhere udp dpt:bootps /* DHCP */
ACCEPT udp -- anywhere anywhere udp dpt:bootpc /* DHCP */
ACCEPT all -- anywhere anywhere state RELATED,ESTABLISHED
REJECT tcp -- anywhere anywhere reject-with tcp-reset
REJECT udp -- anywhere anywhere reject-with icmp-port-unreachable
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain sshguard (1 references)
target prot opt source destination
I’ve tried setting listen: tcp:127.0.0.1:3389 to external IP address of the host as well as an arbitrary IP address from 10.10.182.1/24 network but nothing seems to work after setting the SSH tunnel with ssh -L 3389:localhost:3389 zubmic@192.168.1.248
I’ve also tried with incus network forward commands, but no luck either.
Is it even possible to configure it in a way that I’ve described it? If so, what’s the proper way?
Attaching a diagram in case I wasn’t clear enough about what I would like to do: