In case this helps anyone, here is how this is solved. Sincere thanks to Sai at AWS and the team at AWS who worked on this ticket over several day period.
Caveat this has been tested only when all EC2 instances are in the SAME VPC.
The setup is LXC but it should work for LXD as well.
The goal here is to make the LXC containers on the Ubuntu 16.04 EC2 host generally available on any selected set of ports from the Windows 2012 R2 EC2 instance. It’s a generic solution so it should work with any EC2 instance calling to an EC2 LXC host.
The reference configuration is:
(1)
Ubuntu 16.04 EC2 instance on which LXC containers that have been deployed by Orabuntu-LXC are running. This means the LXC containers are running on an OpenvSwitch network. However this solution should be general for any network solution, not just OpenvSwitch. The containers are on the 10.209.53.0/24 network.
(2)
Windows 2012 R2 EC2 instance.
The LXC containers running on the Ubuntu 16.04 EC2 instance can ping the Windows 2012 R2 EC2 instance, but NOT vice versa.
The problem therefore is to establish communication from the Windows 2012 R2 EC2 instance to the LXC containers on the Ubuntu 16.04 EC2 host on any arbitrary ports.
The solution is as follows:
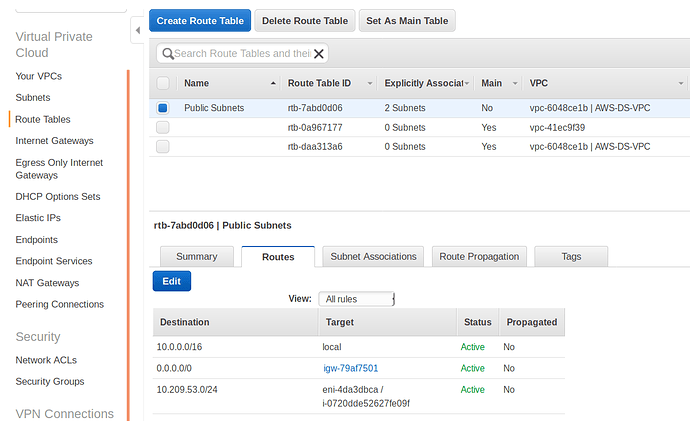
- On the AWS VPC that the EC2 instances are in, go to VPC then to ROUTE TABLES.
- Choose the VPC which is explicitly associated with the subnets to which the EC2 instances belong. Be sure to choose the VPC that is actually associated with the subnets.
- Go to Routes tab and click on big blue “Edit” button to edit routes
- Add a route as follows:
- In the “Destination” field put the CIDR format of your LXC network, e.g. 10.209.53.0/24
- In the “Target” field put the ENI of the adapter of the LXC EC2 host (the Ubuntu16.04 EC2 host)
You can open another window to your EC2 hosts to get this.
Just be sure it’s the ENI for the LXC EC2 host.
The ENI’s have names like this: eni-4da3dbca
When you put the ENI in the “Target” field, it will also grab the instance id and save both into the field, and you will see both of those in the “Target” field. You can double-check that the instance id that it saved is the one that is the LXC host.
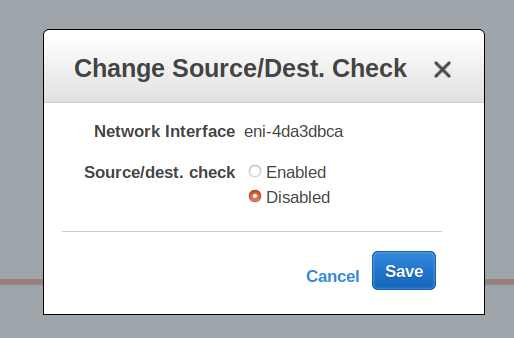
Now you have to do one more setting.
- Go to the EC2 console
- Go to the “Description” tab of the Ubuntu 16.04 EC2 LXC host
- Click on the “eth0” link
- Click on the actual ENI link in the black pop-up dialog (takes you to interfaces page)
- Select the ENI (it should already be selected)
- Go to “Actions”
- Select “Change Source/Dest. Check” from the drop-down menu
- DISABLE source/dest checking.
Now your calling instance, in this case the Windows 2012 R2 EC2 instance, will be able to ping and ssh and pass traffic on any other ports you choose to allow to the LXC containers on the destination EC2 host instance (in this case Ubuntu 16.04 EC2 instance) and vice versa.
Again, sincere thanks to Sai at AWS and the team at AWS who worked on this ticket over several day period.