Hi,
I’m trying to attach guests to a VLAN aware bridge unfortunately I get an error:
Error: Failed to start device “eth0”: VLAN filtering is not enabled in parent bridge “bridge0”
So on Proxmox I had a setup like this
/etc/network/interfaces:
auto lo
iface lo inet loopback
iface eth0 inet manual
iface eth1 inet manual
auto bond0
iface bond0 inet manual
bond-slaves eth0 eth1
bond-mode 802.3ad
bond-xmit-hash-policy layer2+3
auto vmbr0
iface vmbr0 inet manual
bridge-ports bond0
bridge-stp off
bridge-fd 0
bridge-vlan-aware yes
bridge-vids 2-4094
# Primary interface
auto vmbr0.2
iface vmbr0.2 inet static
address 192.168.2.253/24
gateway 192.168.2.1
# Management Interface
auto vmbr0.4
iface vmbr0.4 inet static
address 192.168.4.253/24
gateway 192.168.4.1
vmbr0.2 was the primary interface out onto my network, whilst vmbr0.4 was for management, (web ui ssh etc).
What was really useful is I could attach a VM/Container to vmbr0, and specify the VLAN. As vmbr0.2 is also on the same bridge I was able to access containers from my host. Something which I know I can’t do with a macvlan.
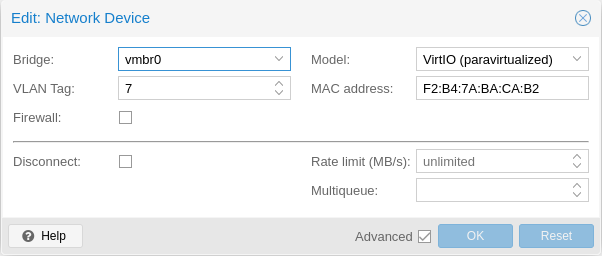
So on my Archlinux server I set up a similar setup, I’ve got a bond0 configured in the same way as the above Proxmox example.
30-bridge0.netdev:
[NetDev]
Name=bridge0
Kind=bridge
[Bridge]
VLANFiltering=false
STP=false
30-bridge0.network:
[Match]
Name=bridge0
[Network]
VLAN=direct
[BridgeVLAN]
VLAN=2-4094
40-vlan2-direct.netdev:
[NetDev]
Name=direct
Kind=vlan
[VLAN]
Id=2
40-vlan2-direct.network:
[Match]
Name=direct
[Network]
Description=VLAN for direct access to gateway
DHCP=true
This setup results in ip -a like this:
ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: bond0: <BROADCAST,MULTICAST,MASTER,UP,LOWER_UP> mtu 1500 qdisc noqueue master bridge0 state UP group default qlen 1000
link/ether xx:xx:xx:xx:xx:xx brd ff:ff:ff:ff:ff:ff
3: bridge0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether xx:xx:xx:xx:xx:xx brd ff:ff:ff:ff:ff:ff
inet6 fe80::xxx:xxxx:xxxx:xxxx/64 scope link
valid_lft forever preferred_lft forever
5: eno1: <BROADCAST,MULTICAST,SLAVE,UP,LOWER_UP> mtu 1500 qdisc mq master bond0 state UP group default qlen 1000
link/ether xx:xx:xx:xx:xx:xx brd ff:ff:ff:ff:ff:ff permaddr xx:xx:xx:xx:xx:xx
altname enp193s0f0
6: eno2: <BROADCAST,MULTICAST,SLAVE,UP,LOWER_UP> mtu 1500 qdisc mq master bond0 state UP group default qlen 1000
link/ether xx:xx:xx:xx:xx:xx brd ff:ff:ff:ff:ff:ff permaddr xx:xx:xx:xx:xx:xx
altname enp193s0f1
7: direct@bridge0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether xx:xx:xx:xx:xx:xx brd ff:ff:ff:ff:ff:ff
inet 192.168.2.253/24 metric 1024 brd 192.168.2.255 scope global dynamic direct
valid_lft 39068sec preferred_lft 39068sec
inet6 2001:db8:xx:xxx:xxxx:xxx:xxxx:xxxx/64 scope global dynamic mngtmpaddr noprefixroute
valid_lft 86174sec preferred_lft 14174sec
inet6 fe80::xxxx:xxxx:xxxx:xxxx/64 scope link
valid_lft forever preferred_lft forever
So now I created some LXD containers, and tried to put it in vlan7 ie:
lxc launch images:ubuntu/22.04 docker-container
sudo lxc profile create vlan7
sudo lxc profile device add vlan7 eth0 nic nictype=bridged parent=bridge0 vlan=7
sudo lxc profile add docker-container vlan7
Error: Failed to start device "eth0": VLAN filtering is not enabled in parent bridge "bridge0"
If I enable VLANFiltering=false on my 30-bridge0.netdev this prevents direct@bridge0 from getting an IP address at all.
I am wondering whether the setup I had in Proxmox is possible in LXD. Only thing I could really find about it was this github issue add support for bridge VLAN filter · Issue #2306 · lxc/lxc · GitHub which sounded very similar to what I am trying to do.