I am trying to provision a router jail that will take care of all of my home networking needs. I am running it inside a jail so that I can ‘save’ on power, but more importantly, it is the same physical box as my workstation so I don’t need to walk (but seriously, it is much quicker to get to).
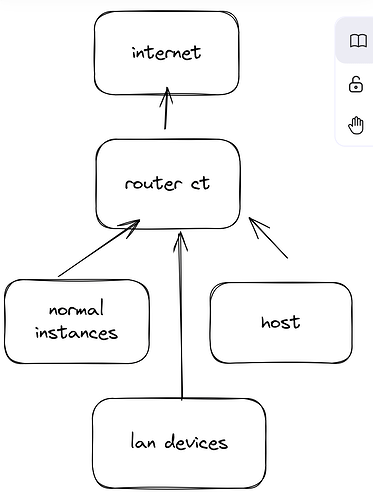
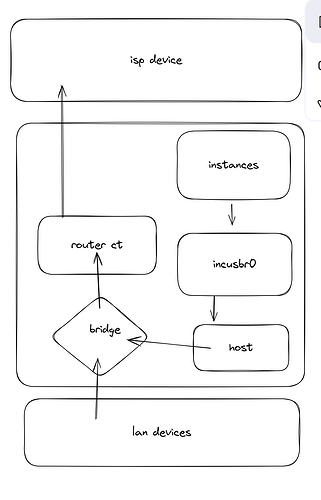
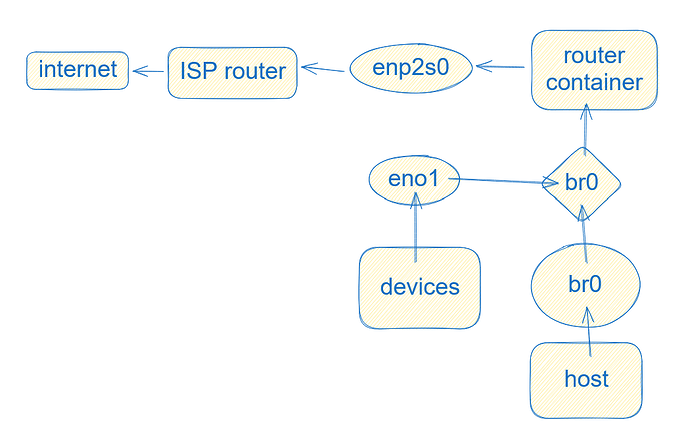
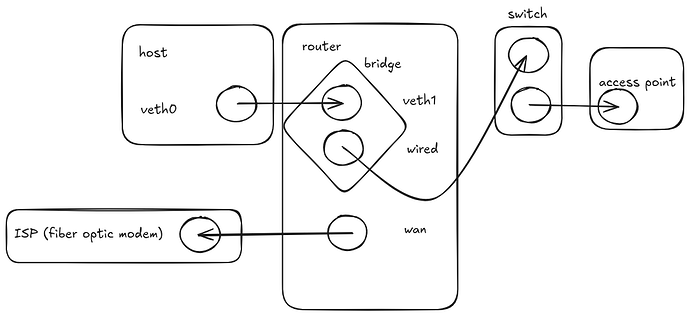
That said, my workstation is the physical host, a desktop computer with 2 NICs. I have assigned both NICs over to the router jail and can see them in the jail:
# incus config device add router wan nic nictype=physical parent=enp2s0 name=wan
# incus config device rm router wan
# incus config device add router wired nic nictype=physical parent=eno1 name=wired
# incus config device rm router wired
Before I cut over to this setup, I have DHCP setup on both interfaces and they’re both on the same subnet.
In the router container, I have modified the resolv.conf such that it points to my upstream DNS server (eventually, it will be 127.0.0.1, but for now, it is on the same subnet). Once I have that set, it is able to get to the Internet just fine.
The last thing I did on the router was to enable IP forwarding:
sysctl -w net.ipv4.ip_forward=1
Now, back to the physical host, the workstation, it only has incusbr0 which is a 10.x.x.x address and a vethXXX interface. I am able to ping the router which is on the other end of that 10.x.x.x address. I updated the default gateway to the incusbr0 ip address of 10.x.x.x and also tried the ip of the router, but no dice:
route add default 10.x.x.x
I can ping the router just fine, but I cannot ping my upstream router nor can I resolve DNS and get to the Internet from the workstation.
I should also mention that my firewall, nftables, is presently empty, so that doesn’t factor in here.
What am I missing here - do I want to use the default gateway as the incusbr0 interface’s IP address because I want all traffic from the workstation to go through the router container. Or, do I want to use the veth interface? The veth interface has no IP address.
I should also mention that I am monitoring traffic on my present router via tcpdump and I don’t see anything being blocked at that level, so I suspect that I am just missing the default route in the right place.
Lastly, for bonus points, eventually, I will want the workstation to be on the same subnet as the wired interface I assigned over to the router. Would I then want to assign incusbr0 to an IP address in my subnet (and the same for eth0 in the router container)?
Thanks for your help.