Weekly status for the week of the 5th September to the 11th September.
Introduction
This past week has seen two of our LXD roadmap items merged; local object storage support using MinIO and restricted.network.access feature in restricted projects. There were also performance improvements for macvlan NICs in VMs and some more improvements to DB query efficiency.
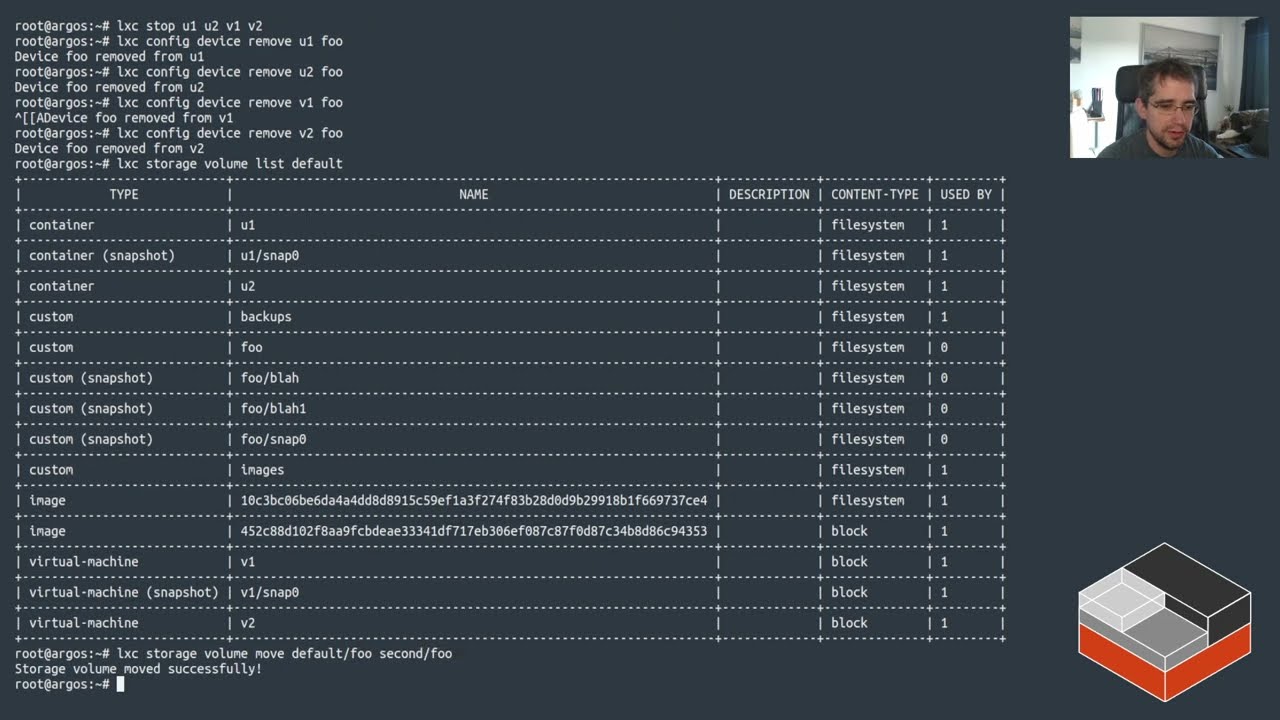
In addition @stgraber has continued his storage themed videos this week by looking at custom storage volumes in LXD:
LXD
New features:
- Local S3 object storage support using MinIO: Following on from the recently added S3 object storage support using Ceph Object Gateway we have now added support for local S3 object storage by leveraging MinIO. For more detail please see Linux Containers - LXD - Has been moved to Canonical and [LXD] Object storage (S3 API).
- Restricted networks access for projects: A new setting has been added for restricted projects (those that have
restricted=trueset) calledrestricted.networks.access. This new setting is a comma-delimited list of network names from the default project that are allowed to be referenced by LXD entities belonging to the restricted project. This setting also controls which networks can been seen in the LXD API when accessed using a restricted project’s context. Additionally the existingrestricted.devices.nicsetting is now also used to control which networks can be accessed from within the restricted project. If set toblockthen no networks can be accessed. If set tomanaged(which is the default if not specified) then only managed networks can be accessed. If set toallowthen all networks can be accessed. Formanagedandallowthe list of networks that can be accessed is then filtered ifrestricted.networks.accessis set.
Improvements:
- Added multi-queue and vhost-net offloading support to
macvlanNICs for virtual machines. - Added profile info to backup index file.
- Removes some functions that loaded storage volume record info inefficiently and replaced with more efficient function usage.
- DB generator improvements to make it more flexible and clearer to use. Also added context support.
Bug fixes:
- Fixed an issue to handle
linux32andlinux64arch personalities inlxc-to-lxdcommand. - Updated AppArmor profile to allow read/write access to
/sys/fs/bpf. - Fixed an issue with extended attribute access when overlay does not filter response.
- Made
dnsmasqstart up failures forbridgenetworks be considered a network start failure. This will cause a warning to be logged inlxc warning listas well as enable automatic retrying to start the network. - Fixed a panic in
lxc alias addwhen no existing client config file exists. - Updated nftables firewall driver to pass rule config via STDIN to the
nftcommand rather than via command arguments so that we don’t hit the argument length limit when using larger rulesets. - Fixed an issue that was causing the
Cachedproperty of an image record to be lost when initializing an image from an existing image in a different project.
Distrobuilder
Improvements:
- Added support for OpenWrt 22.03.
Dqlite (database)
Bug fixes:
- Fixed an issue that caused the
Handovermethod ofApp, to continue looping over other servers after successfully transferring leadership to another server. - Dqlite shell fixes.
YouTube videos
The LXD team is running a YouTube channel with live streams covering LXD releases and weekly videos on different aspects of LXD. You may want to give it a watch and/or subscribe for more content in the coming weeks.
Contribute to LXD
Ever wanted to contribute to LXD but not sure where to start?
We’ve recently gone through some effort to properly tag issues suitable for new contributors on Github: Easy issues for new contributors
Upcoming events
- Nothing planned currently.
Ongoing projects
The list below is feature or refactoring work which will span several weeks/months and can’t be tied directly to a single Github issue or pull request.
- Stable release work for LXC, LXCFS and LXD
- [LXD] Stream lifecycle and log events to Loki
- Infiniband support for VMs
- Dqlite disk-only operation mode
Upstream changes
The items listed below are highlights of the work which happened upstream over the past week and which will be included in the next release.
LXD
- Storage: Object storage with MinIO
- Networks: Adds
restricted.networks.accesssetting - Instance: Load api.Project into instance common struct
- lxd-generate: Create filtered statements from pre-existing “objects” statement.
- Instance: Remove duplicate profiles argument from
instance.Load() - lxc-to-lxd: Handle linux32 and linux64 arch personalities
- VM: Adds support for multi-queue macvlan NICs in VMs
- doc/network/bgp: add some clarifications to the BGP docs
- doc/metrics: add a list of provided metrics
- Add profiles to backup data
- lxd-generate: Refactor
stmtgeneration with more manual intervention - doc/migration: Document lxc-to-lxd tool
- doc/storage/dir: add link to the YouTube video
- lxd/apparmor: allow rw access to /sys/fs/bpf
- GetAllXattr: handle overlay filtering
- Network: Make dnsmasq start failure a network start failure
- Migration cleanup
- lxc: Fix panic when doing
lxc alias addwithout existing config.yaml - doc/migration: clarify how to enable live migration for VMs
- DB: Removes inefficient
storagePoolVolumeGetTypeand associated functions - lxd/db/generate/db/mapping: Use ‘join’ tag to deduce column name
- gomod: Updates dependencies
- Storage: Use a sub-directory for minio on storage volume
- LXD: Add context support to
subprocesspackage - AppArmor: Use non-deferenced outputPath to derive profile name in
archiveProfile - Shared: Don’t modify the global logrus standard logger
- Shared: Update GetAllXattr implementation using github.com/pkg/xattr
- lxd: Fix calls to inst.Project().Name when used in fmt.Sprintf
- lxd-generate: Use
QueryRowContextforGet<entity>ID - Database: Use
QueryContextinquery.Scanandquery.SelectObjects - Database: Replace
tx.Querywithtx.QueryContextandtx.QueryRowwithtx.QueryRowContext - Firewall: Pass nftables rules via stdin rather than as command arguments
- gomod: go mod tidy
- Image: Maintain
Cachedproperty when creating an image in a project from an existing project - Test: Adds
LXD_SKIP_TESTSoption - Lxd-generate: Remove superfluous GetID error check
LXC
- Nothing to report this week
LXCFS
- Nothing to report this week
Distrobuilder
Dqlite (RAFT library)
- Nothing to report this week
Dqlite (database)
Dqlite (Go bindings)
- app: Don’t transfer leadership more than once
- github: Run go test in CI
- Revert “github: Run go test in CI”
- Dqlite demo fixes
- Shell fixes
LXD Charm
- Nothing to report this week
Distribution work
This section is used to track the work done in downstream Linux distributions to ship the latest LXC, LXD and LXCFS as well as work to get various software to work properly inside containers.
Ubuntu
- Nothing to report this week
Snap
- Nothing to report this week